Network
Secure the traffic and internet exposure of your applications with our network interconnection and connectivity, traffic management and load balancing solutions.
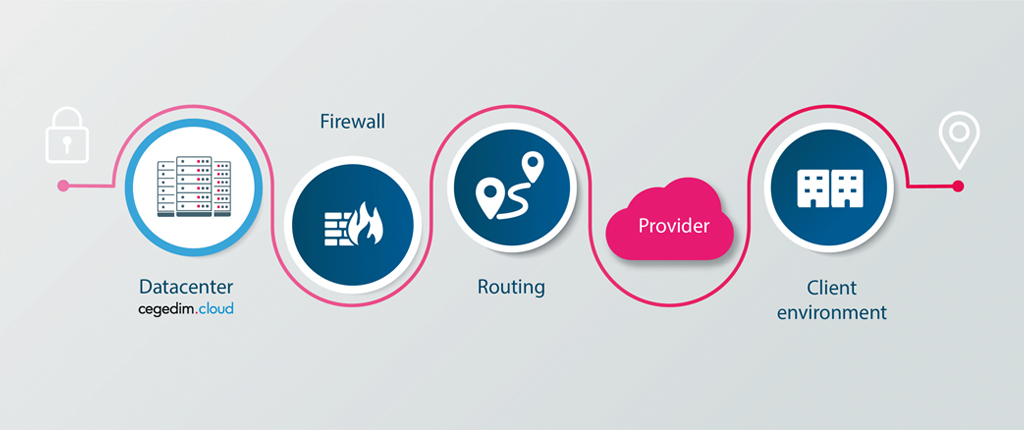
Interconnections
cegedim . cloud hosts more than 300 customer interconnections. We ensure the implementation of a secure and private interconnection between your environments and Cegedim network.
These different interconnection media can be combined and deployed as primary and/or backup interconnection to ensure high availability of the links.
Managed supports
- Managed Dedicated Link Interconnection + Service Provider Link: Managed interconnection to the DC via dedicated physical link
- Managed Site-to-site VPN
Non-managed supports
cegedim . cloud does not intervene on your equipment – unless specifically requested by the customer. We guarantee the availability of our equipment.
- Unmanaged Dedicated Link Interconnection: Unmanaged interconnection to the DC via a physical link; the operator link is at the customer’s expense. Cegedim.cloud provides a secure interconnection to its network via VLAN, and the customer is responsible for bringing back his or her hardware.
- Unmanaged Site-to-site VPN
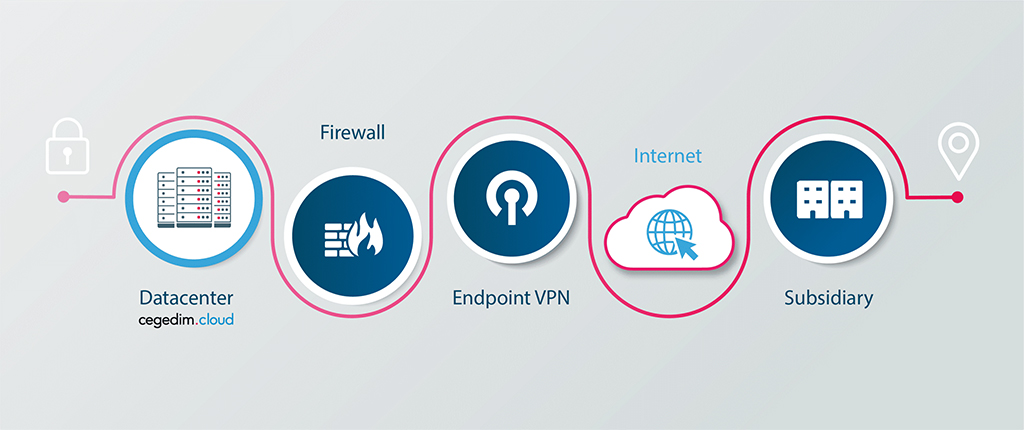
VPN for user
The VPN Ipsec user solution allows you a remote and secure access to your network. You can access all your resources from any remote location through a private, isolated and secure network.
User Ipsec VPN provides the following features:
- Managed service: the deployment, management and maintenance of the platform are ensured by our teams
- Secure TLS connections
- High availability
- Active Directory-based customer authentication
Domain name and certificates
Certificates allow you to secure your applications and sites exposed on the Internet by ensuring the encryption of data in transit between a user and a website. The certificate establishes a secure connection between the web server and the browser. Visitors then access your site through a secure connection indicated by a padlock icon and a URL beginning with the “https” protocol.
cegedim . cloud deploys and manages SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates and offers several types of certificates:
- Standard: issued for a single url
- Wildcard: allows to secure an unlimited number of urls of a domain or sub-domain of your choice
- Multi-Wildcard: unlimited number of urls for several domains and sub-domains on the same certificate
- Extended Validation: offers the highest level of authentication
- Let’s Encrypt: certificates generated by cegedim.cloud and self-managed. These certificates are infinitely renewable.
cegedim . cloud provides a managed service, from domain name provisioning to SSL/TLS certificate management:
- Domain name rental
- Purchase of certificates from certification authorities
- Deployment and lifecycle management, including certificate renewal
Elastic Secured Endpoint
Exposed on the Internet, your applications are particularly exposed to the risks of cyber attacks: botnets, denial of service attacks (DDoS), intrusion, data leakage, etc. Through Elastic Secured Endpoint, cegedim.cloud provides a complete set of technologies for securely exposing your applications on the Internet.
Elastic Secured Endpoint is a fully managed service by our team of security experts. We ensure the deployment, management and reporting of the solution:
- Security and Performance of your applications:
- Encryption/decryption of HTTPS streams
- Intelligent traffic management and load balancing
- Compression and cache management for maximum performance
- Web Application Firewall (WAF) in option
- Security Monitoring:
- Real-time Cyber monitoring of exposed resources on the Internet
- Weekly vulnerability audits
- DDoS Protection:
- Detection and protection against denial of service attacks
Security and performance
Cegedim.cloud load balancers (F5 BIG-IP LTM) provides a deep understanding of the network application traffic and control over how it is managed.
It transforms the chaotic volume of network traffic into logically assembled data flows. Then makes intelligent traffic management decisions, selecting the right destination based on server performance, security and availability.
BIG-IP LTM is a full-featured reverse proxy which allows to inspect, manage and report on your network application traffic. From basic load balancing to complex traffic management decisions based on client, server, or application status, BIG-IP LTM gives you precise control over application traffic.
The SSL acceleration achieved by BIG-IP LTM offloads servers from HTTPS encryption and frees up resources to improve application performance.
Optimized compression and caching management improves interactive application performance, data loading times, and bandwidth utilization.
- Optimization of application speed and reliability
- Improvement of infrastructure performance
- Optimization of the user experience
Features:
Intelligent traffic management decision based on applications and server constraints
Flexibility (scalability of resources on demand)
Real-time analyses (continuity, response time, traffic increase, etc.)
Traffic encryption
Optimized TCP/IP
SSL offloading
Web Application Firewall (F5 BIG-IP ASM)
BIG-IP Application Security Management (F5 BIG-IP ASM) enables organizations to be protected against the 10 greatest OWASP threats, application vulnerabilities and zero-day attacks. With the combination of Layer 7 DDoS defenses, advanced detection and mitigation techniques. As well as dynamic learning, virtual patch execution, and accurate attack visibility, BIG-IP repels even the most complex threats before they reach your servers.
Benefits:
The most effective ready-to-use security
- BIG-IP ASM simplifies policy creation, allowing you to quickly deploy a WAF and provide immediate powerful security. It also adapts policies through automatic learning to counter ever-changing threats hiding in (or targeting) http, https, and WebSocket traffic.
Detailed application visibility and reporting
- Get detailed visibility into policy violations, potential attacks severity, and impact on servers. BIG-IP ASM also uses attack information and reports to identify threats, which become increasingly sophisticated as they evolve.
Fast vulnerability correction
- BIG-IP ASM incorporates Dynamic Application Security Testing (DAST) tools to detect and correct vulnerabilities and unauthorized web changes before code fixes are available.
Market-leading performance and scalability
- Ensure application availability, even under attack, and dynamically improve performance through application optimization and acceleration.
Features:
Protection against Layer 7 attacks
- Detects and reduces application attacks, including DOS and DDOS, brute force, SQL injection, cross-site scripting, remote file insertion, cookie poisoning, and session hijacking.
Equipment identification
- Tracks each visitor’s unique device ID across multiple IPs and sessions and through avoidance actions, for highly accurate blocking of malicious actors.
Proactive defense against robots
- Identifies malicious bots that bypass standard detection methods and reduces threats with greater accuracy, before they begin.
Application Perception
- By associating the application username with attacks, BIG-IP ASM makes it possible to block almost all attacks and better understand them.
Data protection and cloaking (anonymization of data)
- Prevent leakage of sensitive data (credit card information, social security numbers) by completely eliminating data and masking the information.
Incident clustering and attack correlation
- Automatically map multiple attacks into a single incident to improve visibility and facilitate management.
Cyber monitoring
XMCO Serenity is a non-intrusive service for detecting attack attempts and leakage of sensitive information. The service covers all resources associated with the company: IP addresses, domains, brands, names, etc. and detects vulnerabilities in a preventive way. Before they are exploited by hackers: image damage, identity theft, uncontrolled exposure of the IS, data theft and leakage, etc.
- Threat detection and attacks anticipation:
- Sudden exposure of a service or administration interface
- Exposure to an exploitable fault (Heartbleed, Wannacry, Struts…)
- Compromise of a site
- Configuration errors
- Blacklisted IP address referencing
- Exposure of dangerous folders or files within web applications
- Completeness of supervised perimeters:
- “Mastered” perimeters (websites, IP infrastructure, domains)
- “Unmanaged” web perimeters (Cloud services, third-party hosted sites)
- “Unknown” Internet perimeters (forums, non-indexed sites, deepweb)
- Monitoring:
- Daily and qualified alerts
- Customized managerial summaries (choice of indicators, distribution of alerts, evolution of processed tickets, etc.).
- Easy to deploy:
- No log collection
- No agent implementation
- No probe within the IS
Vulnerability audits
Qualys Vulnerability Management is a cloud service that provides immediate and global visibility into the vulnerabilities of your IT systems. And protects you from them. You can identify threats and monitor unplanned changes to your network before they become vulnerabilities:
- Scalable solution that provides comprehensive security coverage for all networks and equipment (internal network, remote or mobile sites, elastic virtual environments)
- Low impact on IT teams in terms of deployment, management and use
- Precise and prioritized results
- Automated weekly scans
- Ongoing supervision and analysis of reports
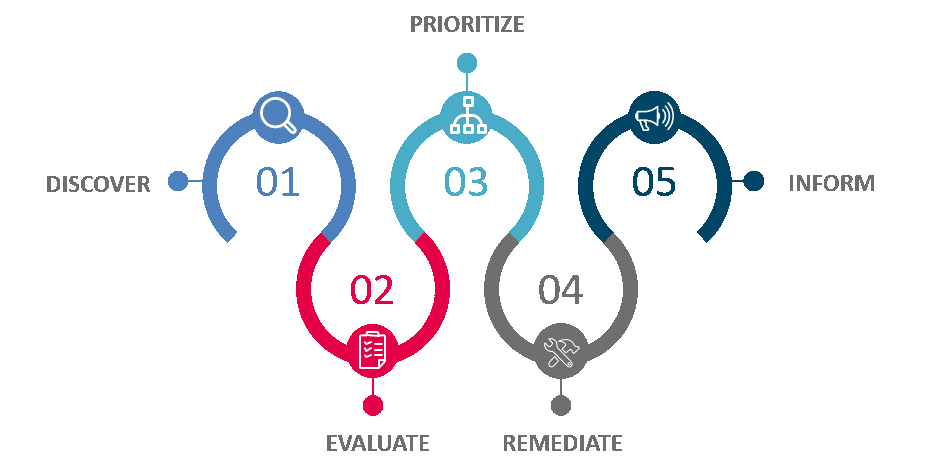
- Easy to deploy:
- No software to install or maintain
- Immediate accessibility from a web browser
- Global on-demand scalability and deployment from a public or private cloud
- Continuous scanning, identification and prioritization of vulnerabilities:
- Network mapping
- Daily and automated updates of the vulnerability knowledge base
- Completeness of reported information: description of the vulnerability, consequence and detailed solution
- Corrective action management: automatic generation and verification of incident tickets, analysis of incident ticket trends and reports, simple instructions to eliminate risks
- Intuitive and comprehensive reporting:
- Management dashboard with global security status summary and instant access to remediation details
- Graphical and trend reports for managers
- Detailed reports with verified remediation actions for technicians
- Constantly updated cloud solution: automatic feature enhancements with transparency for the user
- Integration with other systems via API allowing direct integration with incident ticketing systems and Help Desk solutions
- End-to-end encryption and powerful profile-based access controls to ensure the confidentiality of your security data
Detection and protection against DDoS attacks
cegedim . cloud integrates into Elastic Secured Endpoint a detection and protection solution against DDoS attacks, including very high-capacity attacks, before they reach your network. This service provides multilayer protection (L3-L7), with cloud scanning technologies to detect, identify and prevent threats in real time. While routing legitimate traffic to your site. The fully managed solution is deployed and managed by our security experts.
L3-L7 multilayer protection
Protection against DNS attacks
Protection against volumetric attacks
Routing of legitimate traffic
Detection and protection against DDoS attacks
cegedim . cloud integrates into Elastic Secured Endpoint a detection and protection solution against DDoS attacks, including very high-capacity attacks, before they reach your network. This service provides multilayer protection (L3-L7), with cloud scanning technologies to detect, identify and prevent threats in real time. While routing legitimate traffic to your site. The fully managed solution is deployed and managed by our security experts.
- Protect yourself against phishing proxies, anonymous proxies, botnets, etc.
- Optimize user experience by allowing them to stay online during an attack and minimize any impact on users
- Gain visibility and deep understanding on attacks
Need more information about cegedim.cloud?
If you would like to find out more about cegedim.cloud’s offerings, please contact us and an expert will get back to you as soon as possible.