Security
cegedim.cloud offers many solutions to ensure the security of your data and your employees.
Data Masking
Data Masking is a solution that creates secure copies of databases by desensitizing personal data. Datamasking as a Service allows to meet the challenges of protection, consistency and confidentiality of data by depersonalizing the values, and maintaining structural rules allowing to manipulate data.
Data Masking enables effective desensitization of a data set using comprehensive and flexible masking rules, making it available in different types of environments (analysis, testing, development, etc.):
- Multiple masking techniques: pseudonymization, randomization, scrambling, etc.
- Compliance and security: meeting security and regulatory challenges (e.g. RGPD) related to the processing of sensitive data
- Efficiency, integrity and determinism constraints: maintain consistent data from production data
- Scalability and flexibility: management of large volumes of data for any type of database (Oracle, DB2, SQL Server, Sybase, Teradata)
Define masking rules according to your business needs:
- Adaptability to the environment: masking can be done on site or from a source database to a destination database
- Large pool of masking techniques: substitution, randomization, blurring, regular expression replacement, etc.
Various use cases:
- Use of desensitized test data in non-production environments
- Desensitization of data for transfer to other entities (statistical analysis centers, cohorts, etc.)
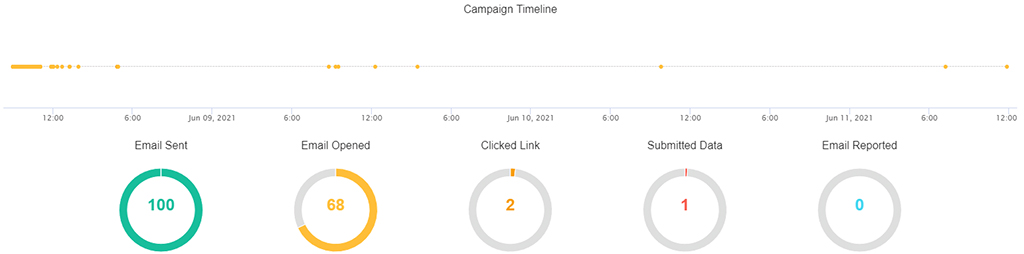
Phishing campaign
Phishing campaigns are used to evaluate the effectiveness of email security awareness. This new service allows you to test the vigilance of your employees:
- Creation of custom email templates
- Testing and programming of the campaign
- Real-time monitoring of campaign statistics and export of results
Advanced Vulnerability Assessment
Advanced Vulnerability Assessment (AVA) allows you to combine a system vulnerability audit with an application vulnerability audit for a 360° view of your security level. The AVA service integrates a set of security tests on selected targets to provide a complete and comprehensive audit report. For each identified vulnerability, the report provides the criticality, description, attack vector, potential impact and solution.
AVA relies on two market-leading and complementary vulnerability audit solutions:
- Qualys Vulnerability Management for system, infrastructure and middleware vulnerabilities (CVE)
– Vulnerability scanning of public and private IP addresses of all components of your application - Acunetix for web application vulnerabilities (OWASP Top 10)
– Dynamic Application Security Testing (DAST) solution
– Unauthenticated scan: testing the resistance of authentication forms, enrolment forms, password resets, etc.
– Authenticated scan: exploitation of internal application functions, data partitioning, elevation of privileges, etc.
– API Scan: Supported API types: SOAP/XML, REST, GraphQL
Identify and fix your security vulnerabilities before others exploit them!
Bot Defense
Bot Defense protects your Internet applications from automated attacks by identifying and mitigating malicious bots.
Bots are automated software designed to perform relatively simple and repetitive tasks on the Internet. One of its main characteristics is that the bot can perform this task at a much higher speed than a human being, 24/7.
Bot Defense relies on two security mechanisms:
- Protection against bots based on reputation and request analysis mechanisms that classify incoming automated requests according to the risk they represent
- Protection against Denial of Service (DoS) attacks targeting the application layers
Depending on the type of threat detected (suspicious/malicious bots), slight or excessive increase in traffic, appropriate responses are automatically provided:
- Generation of a transparent alarm for the user
- Generation of a captcha for the user
- Blocking the request
The Bot Defense solution from cegedim.cloud offers the following main features :
- Managed service: the management of the platform is operated by our teams
- Autonomy and ease of use: activate and deactivate the service, and add IP address exceptions at any time from your ITCare management interface
- Automated service: after a simple click to activate the service, the protection modules against robots and denial of service are automatically deployed
Transparency: access to 3 months of logs generated by Bot Defense
Vault Secret Management
Vault Secret Management provides strong secret encryption, authentication management, authorization management and high availability.
- Secret Management
- Centralize secrets in a secure, highly available space
- Reduce the risk of data leakage and comply with security standards and best practices: passwords are no longer stored or displayed in the clear
- Dynamic secrets: create, renew and revoke secrets on the fly automatically
- Encryption as a Service:
- Encrypt your data on the fly without worrying about managing encryption keys
- Easy encryption key update and rotation
- “API First“: Everything can be controlled via API, in addition to the web interface
- Granular management of profiles and access rights
- Complete traceability of administration actions and access to secrets
Need more information about cegedim.cloud?
If you would like to find out more about cegedim.cloud’s offerings, please contact us and an expert will get back to you as soon as possible.